|
The course HARDWARE 2: Server, network and communications from YBET |

|
| YBET | Computer hardware training | Contact |
3. Base for network computing transmission
1. Wiring Ethernet - 2. Physical connection - 3. Bus topology - 4. Ring topology - 5. Star topology - 6. Mixed topology - 7. mesh network topology - 8. Access method
To communicate information between computers and data-processing peripheral, various concepts are necessary. Before talking about the connections networks, let us begin for the pleasure with a current communication between a computer and a ... printer.
In a parallel connection, each bits constituting a byte (byte) are transferred at the same time. This connection consists of 8 wire of data and various wire of mass, more of the signals of communications (out of paper...). To make pass a data byte from the computer to the printer, we send on these 8 lines a tension or not according to the binary message to send. To know if a message is sent, the printer only makes look on 8 data connections: if a tension is present or not. This does not require in theory of signals of controls. Now, the parallel connections are supplanted by serial connections. This replacement is related on the price of physical connections and the obstruction of wire. If copper is not too expensive, the installation by an electrician is more expensive and lot of wire for parallel connections would quickly become unmanageable.
In a serial connection, one finds at the beginning only one wire of communication (two for the bi-directional one) and a ground wire. In practice, others wire are used for the control of the communications. The principle is the same one as above, except that the 8 bits of data will pass on only one line in turn. The computer sends on a wire specialized an electric signal (tension) which announces to the receptor that one sends of data will occur and this one prepares to look at what occurs on the cable. If a tension is present, the received signal is the 1, if no signal is present, the received signal is 0. The various signals are sent following the other, which explains why the connection series is considered slow.
As soon as a computer sends a signal to another, the data must be controlled. A solution would be to require of the receptor to return the data received for checking. The importance the speed of transfer makes this principle null. In practice, one carries out a parity check. To calculate the parity, one hopes the number of 1. If this number is even, the parity is 0, if it is odd, the parity is 1 in the case of an even parity, EVEN (the reverse in a parity ODD, odd). One sends like ninth bit this equal number. This checking of the data is not completely reliable. If two bits are bad, the parity check is right, whereas the received signal is false. In the space connections at long distances, the number of bits of parities increases. This system of parity is often used in the modems, but more in the systems networks. These concepts were already seen in first years.
In our parallel or serial connection, only two computers are connected together. Physical connection (cabling) must connect more computers between-them. Each one must also speak in its turn to prevent that several signals are present at the same time. This east governs by the type of network.
How computers of the different types can be included/understood at the time of the data transmission in network? What one sends like continuation of 0 and of 1 component the message is called a trame. It is consisted of the data and the headings and end of messages added by the layers of OSI model or Internet. These trames are organized specific manners according to a protocol.
A protocol is the way in which information is sent towards the recipient. As in the human language, the shipper must use the same language (protocol) that the recipient so that the exchange of information is correct. The most current protocols is TCP/IP, IPX, NetBeui for old computing network. In this course, the protocols really do not intervene in the hardware part of the networks (with share for the routing). Indeed, in OSI model of chapter 2, we limit ourselves to the first 3 levels, whereas the protocol is related to level 4: transport.
1. Ethernet cabling
The cabling of the local area networks tends today to be standardized, and not to be distinguished from the data-processing and telephone wiring general of the company. Three media are used today in the local area networks.
1.1. The telephone twisted pair
not very expensive, rather easy to pose, it is today the most widespread support for the local area networks. They is often taken again under the term Ethernet network or network RJ45
The type of cable used determines the maximum speed of transmission of the data, as well as the standard of connection of the networks. In the case of the twisted pair, one uses telephone cable. Nevertheless, these cables are taken again according to their physical characteristics (diameter, insulator, length of the twists) in various categories below:
Type of cable |
Supported speed |
Type of network |
Category 1 |
Telephony |
Telephony |
Category 2 |
1 Mbps |
Token Ring and telephone |
Category 3 |
16 Mbps |
Token Ring and 10 base T |
Category 4 |
20 Mbps |
10 Base T |
Category 5 |
100 Mbps |
10BaseT and 100 Base TX |
5e category (category 6) |
1 Gbps |
Giga Ethernet |
There are 2 families of cables of twisted pairs. Shielded cables (STP: Shilded Twisted pair) are surrounded of an aluminum foil to make electrostatic screen. Cables UTP (Unshielded twisted pair) do not have any. Most current are the UTP.
1.2. The coaxial cable
Definitely expensive, is in loss speed after having been the support par excellence of the first local area networks which functioned in broad band mode (band-width cut out in beaches of frequency, each one being allotted to a channel). Today, the majority of the local area networks functioning in baseband (all the transmitting stations on the same channel occupying the totality of the band-width), the coaxial cable are less necessary and one employs it almost only for the interconnection of various local area networks or in environments disturbed by spurious electromagnetic signals (electric motor for example).
 The sheath makes it possible to protect the cable from the
external environment. It is usually out of rubber (sometimes out
of polyvinyl Chloride (PVC), possibly out of Teflon)
The sheath makes it possible to protect the cable from the
external environment. It is usually out of rubber (sometimes out
of polyvinyl Chloride (PVC), possibly out of Teflon)
- The shielding (metal envelope) surrounding the cables makes it possible to protect the data transmitted on the support of the parasites (otherwise called noise) which can cause a distortion of the data.
- The insulator surrounding the central part consists of a dielectric material making it possible to avoid any contact with the shielding, causing electric interactions (short-circuit).
The heart, achieving the task of data transmission, is generally made up of only one bit out of copper or several twisted bits.
1.3. Fiber optic cable
Significantly more expensive, fiber allows high flow rates. Using a light signal, it is immune to electromagnetic interference. It is used primarily to interconnect LANs or over long distances. This support is fragile, difficult to install and breaks easily under an effect of torsion.
The optical fiber has several advantages:
- Light
- Perfect immunity to electromagnetic interference
- Low attenuation of the signal with the remote
- Accepts larger than 10 Gb/s speeds
- High band width, of a few tens of MHz to several Ghz (in single-mode fiber).
The fiber cabling is often used for connections between several buildings (called backbone) and long distances (from a few kilometers to 60 km for single mode fiber). This type of cable does not listen on the cable, it emits no electromagnetic signal during data transfer. Two types of fiber optic are used:
- Single-mode fiber (SMF) uses a single channel of transfer within the driver and allows transfers up to 100 Gb/s per kilometer. The path is perfectly linear, there is no dispersion of the signal. On the other hand, the emission source is a laser diode, more expensive and more difficult to implement.
- Multi-mode (MMF) uses a simple least expensive LED diode but with a non linear signal. Rays use different path depending on the angles of refraction and so different time of propagation: the signal needs to be rebuilt upon arrival. Mainly used for internal networks, performance is of the order of the Gb/s.
2. Network's topologies
Before learning the various forms of connections, let us see the type of connections, called topology.
There are three principal types of topologies:
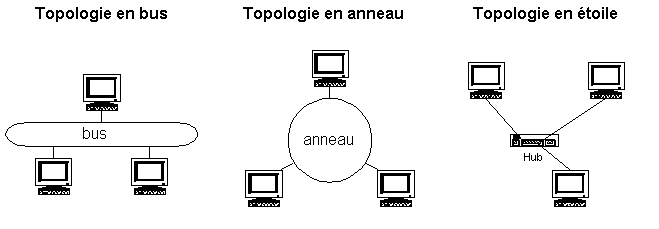
3. Topology bus network
The bus, a central segment where information circulates, extends over the entire length from the network, and the machines come to cling to it. When a transmitting station data, they circulate over the entire length of the bus and the destination station can recover them. Only one station can emit at the same time. In end of bus, a "terminator resistor" makes it possible to remove information definitively so that another station can emit.
The advantage of the bus is that a broken down station does not disturb the remainder of the network. It is, moreover, very easy to set up. On the other hand, in the event of rupture of the bus, the network becomes unusable. Also let us note that the signal is never regenerated, which limits the length of the cables.
This topology is used in the networks Ethernet 10 Base 2 and 10 Base 5.
4. Ring topology
Developed by IBM, this architecture is mainly used by the networks Token Ring. Token Ring uses the technique of access per "token". Information circulates of stations in stations, while following the ring. A token circulates around the ring. The station which has the token transmits data which make the turn of the ring. When the data return, the station which sent them eliminates them from the network and passes the token to its neighbor, and so on...
This topology makes it possible to have a flow close to 90% of the band-width. Moreover, the signal which circulates is regenerated by each station. On the other hand, the breakdown of a station returns the whole of the unusable network. The interconnection of several ring is not easy to implant. Lastly, this architecture being the property of IBM, the prices are high and almost non-existent competition.
This topology is used by networks Token Ring and FDDI.
Note: during 2000, IBM announced that it would not follow any more a development of integrated circuits for this type of bus.
5. Star topology.
It is the most current topology, in particular with the networks Ethernet RJ45. All the stations are connected to single composing central: the network concentrators. When a transmitting station towards the concentrator, this one sends the data to all the other machines (hub) or only to the recipient (switch).
This type of network is easy to set up and to supervise. The breakdown of a station does not blame the whole of the network. On the other hand, one needs more cables than for other topologies, and if the concentrator breaks down, all the network is destroyed. Moreover, the practical flow is worse than for other topologies.
This topology is used by the networks Ethernet 10, 100 Base T and following.
6. Mixed topology.
A topology as above is unfortunately too simplistic in the case of important networks. If a star topology is perfect in the case of a geographically limited network, a world network cannot use a connection of this type. The method used is thus to connect star distribution systems (by buildings for example) via connections in the bus (telephone for example).
In the continuation of the course, by interesting us in connections internetwork, we will re-examine this type of space-division switching, by knowing that each part of the network is generally out of star.
7. Mesh network topology.
The ring main systems (represented here by computers) are connected by routers who choose the best way according to several possible. Internet is a topology with a grid, this guarantees best stability in the event of breakdown of a node but is difficult to implement, mainly on the level of the choice of the roads to follow to transfer information. This requires the use of intelligent routers.
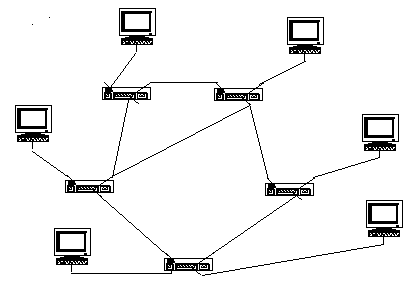
This topology cannot be used in the internal networks using Ethernet.
8. Access method
"to put order" in a local area network, where all the computers can take the initiative of the sendings of messages, one needs a rule complied with by everyone. It is the access method. One distinguishes two principal methods, the application and the token. They distinguish both principal family from local area networks: Ethernet, which uses the application, and the token ring (Token Ring of IBM), "deterministic" method (nonrandom).
The two methods are standardized within the framework of American IEEE association (committee 802), standardization included within the framework of the ISO. If one refers to OSI model, which distinguishes the access methods is located of course in layer 1 (Physical layer) of OSI model, since wiring and topologies are different, but especially in a lower underlayer of layer 2 of OSI model (Data link) called Mac (Medium Access Control). The method Ethernet CSMA/CD (Multiple Sense Carrier Access With collision Detection) is standardized under name 802.3 and the token ring under 802.5.
In the Ethernet method, using the application, each computer sends its message without occupying itself too much from what occurs on the cable. If a transmitting station while another is emitting, this causes a collision thus. The second transmitting station stops the transmission to start again later. In the case of Giga Ethernet, the stations does not send any more the message, but a starting signal to check if the way is free. The CSMA/CD (Multiple Sense Carrier Access with Collision Detection) takes care of the detection of the collisions.
In the token method , each station can communicate in its turn. If 3 computers are connected out of ring, station 1 speaks, then the 2, then the 3. Station 1 can again speak, and so on.
In relation:
- Ethernet switch, Hub and routers: Ethernet concentrators for computing networks
- Networks architecture Example for physical connection
|
Next of hardware 2 course > Chapter 4: Network and Ethernet Cards |
The "Hardware 1" course: Computer and peripherals, the "Hardware 2" course: Network, servers and communication.
For the whole of the hardware training.
© YBET IT 2006 - 2017